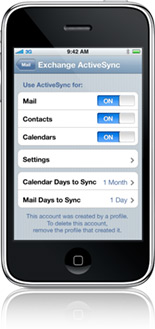
Apple implemented device encryption in the iPhone 3GS, improving its odds of being considered for enterprise deployment.
However, users using Exchange ActiveSync (EAS) to connect to their Exchange 2007 mailboxes couldn't take advantage of it, even when encryption was required by an
Exchange ActiveSync Mailbox Policy, because the device didn't tell Exchange it can support encryption.
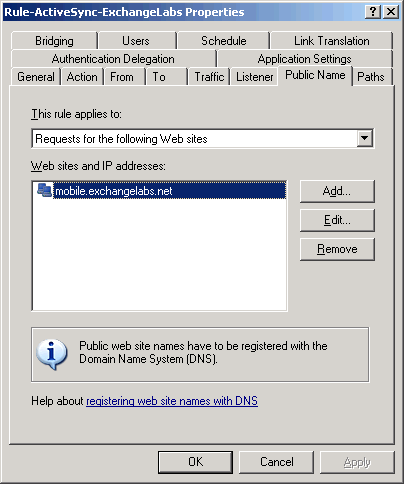
With the latest iPhone OS 3.1 update, iPhones start identifying themselves correctly, and if the ActiveSync policy configured by the administrator requires device encryption (see Figure 1 below), data on the device is encrypted. That's great news— unless you happen to have an
older iPhone. If you're using the
(Original/Classic/2G/1G?) iPhone , or the iPhone 3G, and device encryption is required, you will be unable to log on to your mailbox.
This is great for iPhone 3GS users, who can now be more secure than they previously were. Users of
legacy iPhones can either buy an iPhone 3GS to have their data stored securely on the device, or
downgrade, somehow, to the previous version of iPhone OS. I'm not sure if a downgrade is possible, or if you'll need to take your iPhone to an Apple store to have it downgraded.
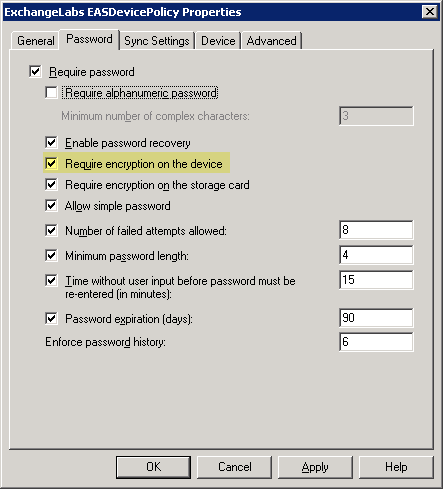 Figure 1: Enforcing device encryption using an ActiveSync Mailbox Policy in Exchange 2007
Figure 1: Enforcing device encryption using an ActiveSync Mailbox Policy in Exchange 2007News.com's Jim Dalrymple suggests in
Apple explains iPhone OS 3.1 Exchange changes:
If you already upgraded to iPhone OS 3.1 on an iPhone or iPhone 3G and connect to an Exchange 2007 server, you can ask that the IT admin turn off the hardware encryption requirement for those devices.
Good luck with that!
Update: Interestingly, the above suggestion is actually what Apple recommends in its knowledgebase article
TS2941: iPhone OS 3.1: 'Policy Requirement' error when adding Microsoft Exchange account. Specifically:
To reestablish syncing, have your Exchange Server administrator change the mailbox policy to no longer require device encryption.
In a nutshell— lower security to allow older iPhones to sync. If you use the same ActiveSync policy for all users, this also lowers security for all mobile devices in your organization!
If you want to read InfoWorld
(the dabbling-in-sensationalism publication I call MAD magazine of tech journalism and others equate with tabloid journalism) executive editor Galen Gruman's - should I say, more strongly worded take on it, here it is.
It turns out that Apple's iPhone 3.1 OS fix of a serious security issue -- falsely reporting to Exchange servers that pre-3G S iPhones and iPod Touches had on-device encryption -- wasn't the first such policy falsehood that Apple has quietly fixed in an OS upgrade. It fixed a similar lie in its June iPhone OS 3.0 update. Before that update, the iPhone falsely reported its adherence to VPN policies, specifically those that confirm the device is not saving the VPN password (so users are forced to enter it manually). Until the iPhone 3.0 OS update, users could save VPN passwords on their Apple devices, yet the iPhone OS would report to the VPN server that the passwords were not being saved.
I resisted highlighting that entire quote. Needless to say, if this is indeed true and not merely InfoWorld's
interesting interpretation and reporting of facts— it makes Apple's tall claims of being "
highly secure by design" and "
secure from day 1" across its product line (OS X, Safari browser, the iPhone and Apples online services) worth every bit of suspicion, skepticism, and scrutiny they deserve.
The InfoWorld article ends with:
IT organizations can also consider using third-party mobile management tools that enforce security and compliance policies; several now support the iPhone to varying degrees, including those from Good Technology, MobileIron, and Zenprise.
Although mobile device management products such as those mentioned above can make it cost-effective to manage large number of mobile devices, improve service levels, lower time to resolution, and to some extent help with securing them, I doubt any of them can actually determine if what the device reports about its capabilities or status is really true. To read rest of the article, head over to
The other iPhone lie: VPN policy support on InfoWorld.com.
Does the iPhone meet the bar for enterprise deployment? Do you allow iPhone users to connect to your Exchange server?
Labels: Exchange Server 2007, Mobility - BES/ActiveySync, Security

 Exchangepedia Blog is read by visitors from all 50 US States and 150 countries world-wide
Exchangepedia Blog is read by visitors from all 50 US States and 150 countries world-wide
 Apple implemented device encryption in the iPhone 3GS, improving its odds of being considered for enterprise deployment.
Apple implemented device encryption in the iPhone 3GS, improving its odds of being considered for enterprise deployment. 
 The Obama campaign executed well on several fronts. BarackObama.com was voted as the best campaign website by the
The Obama campaign executed well on several fronts. BarackObama.com was voted as the best campaign website by the 
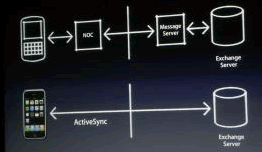 Phil Schiller, Apple's Senior VP of Marketing, announced minutes ago what many have suspected all along - Apple chose to go with Microsoft by licensing EAS. Schiller demonstrated EAS on the iPhone, including the ability to remotely wipe an iPhone.
Phil Schiller, Apple's Senior VP of Marketing, announced minutes ago what many have suspected all along - Apple chose to go with Microsoft by licensing EAS. Schiller demonstrated EAS on the iPhone, including the ability to remotely wipe an iPhone. March 6 is here, and the iPhone's software roadmap, including the much talked about "enterprise features" should be public in a few hours, along with the release or another announcement of the iPhone SDK.
March 6 is here, and the iPhone's software roadmap, including the much talked about "enterprise features" should be public in a few hours, along with the release or another announcement of the iPhone SDK.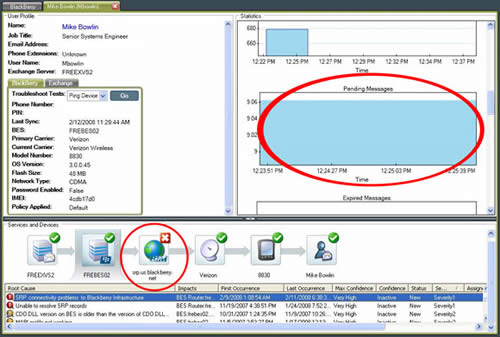










 The end-to-end view of BlackBerry® service provided by Zenprise has always been of
The end-to-end view of BlackBerry® service provided by Zenprise has always been of  The exciting news - standing here during the attendee party at TechEd 2006, I couldn't have thought of this possibility. Yes! The
The exciting news - standing here during the attendee party at TechEd 2006, I couldn't have thought of this possibility. Yes! The 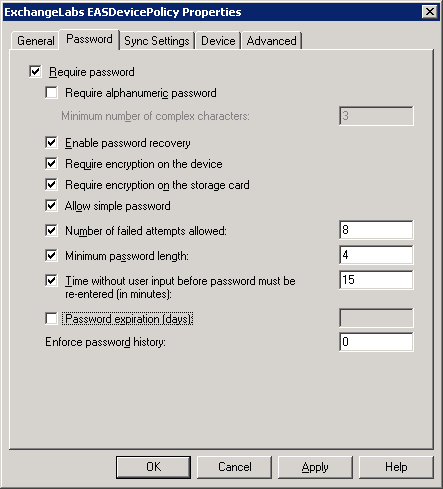
 Has Apple finally seen the light, and licensed Exchange ActiveSync from Microsoft? Will iPhone users be able to get Exchange email pushed out to their iPhones using DirectPush?
Has Apple finally seen the light, and licensed Exchange ActiveSync from Microsoft? Will iPhone users be able to get Exchange email pushed out to their iPhones using DirectPush?  An interesting week in Orlando, as
An interesting week in Orlando, as