cc:Betty: A cool web app you may want to block
Posted by Bharat Suneja at 11:50 AM
It's also amazingly simple to use. Besides adding content on the cc:Betty web site, users can simply add [email protected] as an additional recipient (To/Cc/Bcc) to email they send, and it shows up in their cc:Betty account - email content, attachments, et al. With the click of a button, users can publish the discussion to their Facebook feed.
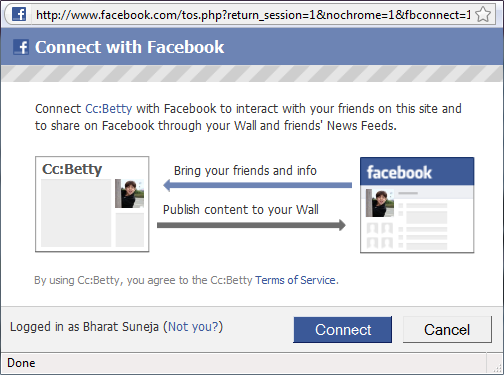
Figure 1:With the click of a button, cc:Betty posts your discussion to your Facebook profile
And therein lies the threat to your data!
Although it's an impressive tool for personal use (the usual caveats about personal information and privacy apply), organizations and IT departments must consider the consequences carefully. Many small businesses and organizations operating in unregulated industries or locales may not consider themselves to be at risk and actually welcome such services.
If your organization isn't one of them, consider that simply adding another recipient to all email messages results in data leakage. How's this any different from adding any other recipient to an email? Unlike other recipients, the sole purpose of cc:Betty is to facilitate further sharing of email content outside an organization. Email can contain sensitive information— including high business impact (HBI) data or personally identifiable information (PII). Transmitting and storing such information outside the organization, with no control over the content or its security, could expose your organization to multiple risks.
It's important to consider what services such as cc:Betty do with your information. cc:Betty's privacy policy is not very different from Gmail's privacy policy— email content is scanned to display relevant ads. Some would argue that similar content scanning is also performed by antispam and antivirus software and services, and that this isn't something to be concerned about.
Regardless of whether you find content scanning by an automated process acceptable or not, the bigger threat is data leakage.
What can cc:Betty do to help organizations?
How can cc:Betty help organizations protect themselves from unauthorized use of its service? As a web-based service its success lies in widespread adoption of its app. More users, more user content accumulated, more sticky the service proves to be, and more pageviews it racks up. As such, there's no incentive to actually stop users from joining or posting information. In fact, it may directly impact its success.
However, cc:Betty and other such services may gain a lot of goodwill and more acceptance if they work with organizations to help prevent data leakage. One way of doing this may be to block email from organizations that register with it. When a user signs up for an account using your organization's email address, he/she gets a polite message about your company not allowing use of the service. Email sent from your domain can also be bounced back with a polite NDR.
Some organizations may choose to allow their users to use the service, but with appropriate policy guidelines and controls in place. [Update: According to cc:Betty, an enterprise version of the service is in the works.]
Does your organization allow the use of cc:Betty.com or similar services?
Labels: Compliance, Exchange 2010, Exchange Server 2007, Rights Management, Security

 Exchangepedia Blog is read by visitors from all 50 US States and 150 countries world-wide
Exchangepedia Blog is read by visitors from all 50 US States and 150 countries world-wide
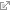
 Are you involved with e-Discovery (aka "electronic discovery") as a consequence of litigation, regulatory audit or perhaps an internal investigation? Whether you've been hit by litigation or not, it's important for messaging professionals to know about e-Discovery, and be prepared for it. Mimosa Systems, the Santa Clara-based archiving software company, has an e-Discovery guide that's very well produced and fun to read. It actually makes the wrapped-in-legalese e-Discovery process interesting— a far cry from the scores of mundane publications and articles produced on the subject. Chances are after reading it you may even look forward to an e-Discovery request! Head over to the Mimosa Systems web site to download
Are you involved with e-Discovery (aka "electronic discovery") as a consequence of litigation, regulatory audit or perhaps an internal investigation? Whether you've been hit by litigation or not, it's important for messaging professionals to know about e-Discovery, and be prepared for it. Mimosa Systems, the Santa Clara-based archiving software company, has an e-Discovery guide that's very well produced and fun to read. It actually makes the wrapped-in-legalese e-Discovery process interesting— a far cry from the scores of mundane publications and articles produced on the subject. Chances are after reading it you may even look forward to an e-Discovery request! Head over to the Mimosa Systems web site to download 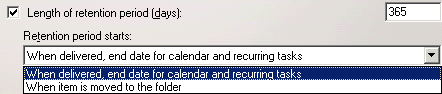
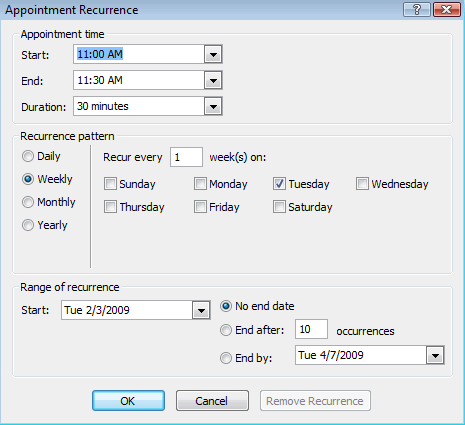

 An existing Recipient Policy can be modified to add/remove Mailbox Manager or Email Address settings by right-clicking the policy and selecting Change property pages.
An existing Recipient Policy can be modified to add/remove Mailbox Manager or Email Address settings by right-clicking the policy and selecting Change property pages.
 From the Property Pages dialog box, select the appropriate settings to be included in the Recipient Policy.
From the Property Pages dialog box, select the appropriate settings to be included in the Recipient Policy.