Exchange Server 2007: Renewing the self-signed certificate
Posted by Bharat Suneja at 7:42 AM
The self-signed certificate meets an important need - securing communication for Exchange services by default. Nevertheless, one should treat these self-signed certificates as temporary. It's not recommended to use these for any client communication on an ongoing basis. For most deployments, you will end up procuring a certificate from a trusted 3rd-party CA (or perhaps an internal CA in organizations with PKI deployed).
However, should you decide to leave the self-signed certificate(s) on some servers and continue to use them, these need to be renewed - just as you would renew certificates from 3rd-party or in-house CAs.
 To renew the certificate for server e12postcard.e12labs.com, a server with CAS and HT roles installed:
To renew the certificate for server e12postcard.e12labs.com, a server with CAS and HT roles installed:Get-ExchangeCertificate -domain "e12postcard.e12labs.com" | fl
Note the services the certificate is enabled for (by default: POP, IMAP, IIS, SMTP on CAS + HT servers). Copy the thumbprint of the certificate.Get a new certificate with a new expiration date:
Get-ExchangeCertificate -thumbprint "C5DD5B60949267AD624618D8492C4C5281FDD10F" | New-ExchangeCertificate
If the existing certificate is being used for SMTP, you will get the following prompt:Confirm
Overwrite existing default SMTP certificate,
'C5DD5B60949267AD624618D8492C4C5281FDD10F' (expires 8/22/2008 7:20:34 AM), with certificate '3DA55740509DBA19D1A43A9C7161ED2D0B3B9E3E' (expires 1/28/2009 7:37:31 AM)?
[Y] Yes [A] Yes to All [N] No [L] No to All [S] Suspend [?] Help
(default is "Y"):
Thumbprint Services Subject
---------- -------- -------
3DA55740509DBA19D1A43A9C7161ED2D0B3B9E3E ..... CN=E12Postcard
Get-ExchangeCertificate -thumbprint "3DA55740509DBA19D1A43A9C7161ED2D0B3B9E3E" | fl
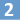 The old certificate is enabled for IIS, POP, IMAP and SMTP. The new certificate generated using the above command is enabled only for POP, IMAP and SMTP - IIS is missing.
The old certificate is enabled for IIS, POP, IMAP and SMTP. The new certificate generated using the above command is enabled only for POP, IMAP and SMTP - IIS is missing. To enable the certificate for IIS:
Enable-ExchangeCertificate -thumbprint "3DA55740509DBA19D1A43A9C7161ED2D0B3B9E3E" -services IIS
This enables the certificate for IIS (in addition to any other services it may already be enabled for - it adds to existing values of the services property). Test services are working with the new certificate. If it works as expected, the old certificate can be removed:
Test services are working with the new certificate. If it works as expected, the old certificate can be removed:Remove-ExchangeCertificate -thumbprint "C5DD5B60949267AD624618D8492C4C5281FDD10F"
Related posts:- Outlook Anywhere and Exchange's Self-Signed Certificate
- Which name should I use as Common Name for my UC certificate?
- DigiCert: A Certificate Authority with excellent customer service
Labels: Administration, Exchange Server 2007, Exchange Shell, OWA, Security, SMTP

 Exchangepedia Blog is read by visitors from all 50 US States and 150 countries world-wide
Exchangepedia Blog is read by visitors from all 50 US States and 150 countries world-wide