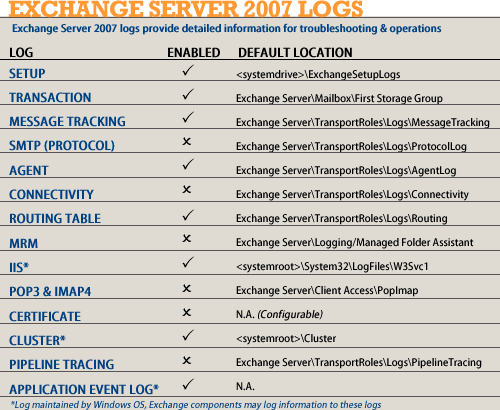
A recent question got me thinking about this, thanks to a fellow MCT. How may logs does Exchange Server 2007 have? There are the known logs, carried over from previous versions (albeit with some differences), and a slew of new logs that one deals with.
So let's take a quick look at the number of logs the mighty new
(well, almost... ) Exchange Server 2007 has. Pointers to previous posts or relevant Exchange documentation are provided throughout this post for additional information.
1. Setup Log: Exchange Server 2007 logs detailed setup-related information to the Setup log. Two log files are created in
\ExchangeSetupLogs directory - 1)
ExchangeSetup.msilog logs events related to extraction of Exchange files from the installer 2)
ExchangeSetup.log has details about every step of the setup, including system status, pre-requisite checks, installation, configuration, etc. A shell script
Get-SetupLog.ps1 (in the
\Exchange Server\Scripts directory) is available to review setup information. More details in '
Verifying an Exchange 2007 Installation" in product documentation.
2. Transaction logs: These are the familiar ESE Database write-ahead logs that we've seen since as long as Exchange's ESE Databases have been around. These contain information about changes to the Exchange (Mailbox and Public Folder) Databases.
In addition to the Mailbox and Public Folder Databases, Exchange Server 2007 also uses ESE databases for transport queues.
Transaction logs used to be 5 Mb. in previous versions. In Exchange Server 2007, the size has been reduced to 1 Mb. to accommodate new replication features. It's important to note that
transaction logs belong to a Storage Group, not a particular Mailbox or Public Folder Database.
Unlike most other logs mentioned in this article, transaction logs don't contain any readable information that can be readily used for troubleshooting Exchange issues. However, these are perhaps the most important type of logs for the health of an Exchange server. More information about transaction logs in "
Understanding transaction logging".
Transaction log-related configuration changes can be made using the
Set-StorageGroup shell command. Basically, there's not much to configure, except changing the path to move transaction logs to an alternate location - a different folder or on another volume. You can enable Circular Logging in scenarios where up-to-the-minute restores are not required, or during bulk mailbox moves where generation of an extraordinary number of log files is anticipated.
Parameters and defaults:
LogFolderPath: location of transaction logs for a Storage Group
CircularLoggingEnabled: false
LogFilePrefix: View-only parameter. Prefixes are added to transaction log file names, starting with E00 for log files belonging to the first Storage Group on a server, incremented sequentially to E01, E02, etc. for subsequent Storage Groups.
LogFileSize: View-only parameter. 1024 (file size in bytes).
CopyLogFolderPath: location of transaction logs for LCR replicas
3. Message Tracking Logs: Message Tracking logs tell us where a message is at every step of the way in the transport pipeline. These are invaluable for troubleshooting mail flow problems. Many third-party reporting tools also use these as fodder to generate great-looking reports about messaging activity in Exchange environments. (Read previous post "
Exchange Server 2007: Message Tracking from the command line")
Message Tracking logs exist on mailbox and transport servers (Hub and Edge Transport) and are enabled by default. The relevant parameters (listed below) can be viewed/modified using
Get-TransportServer/Set-TransportServer commands. The Mailbox server equivalents are
Get-MailboxServer/Set-MailboxServer.
Parameters and defaults:
MessageTrackingLogPath: \Exchange Server\TransportRoles\Logs\MessageTracking
MessageTrackingLogEnabled: true
MessageTrackingLogSubjectLoggingEnabled: true
MessageTrackingLogMaxAge: 30.00:00:00 (30 days)
MessageTrackingLogMaxFileSize: 10Mb
MessageTrackingLogMaxDirectorySize: 250Mb
Access: Get-MessageTrackingLog shell command, or the Message Tracking tool in EMC.
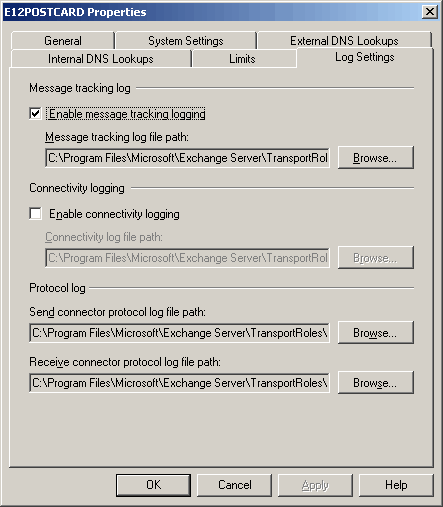 Figure 1: The EMC allows you to enable/disable Message Tracking and Connectivity logs, and set or change paths where the log files are stored for these, in addition to SMTP Send and Receive logs. To access the above dialog box, expand Server Configuration | Hub Transport | select a Hub Transport server | select Properties | go to Log Settings tab.4. SMTP Send and Receive Logs (aka "Protocol" logs):
Figure 1: The EMC allows you to enable/disable Message Tracking and Connectivity logs, and set or change paths where the log files are stored for these, in addition to SMTP Send and Receive logs. To access the above dialog box, expand Server Configuration | Hub Transport | select a Hub Transport server | select Properties | go to Log Settings tab.4. SMTP Send and Receive Logs (aka "Protocol" logs): Exchange Server 2003/2000 have a single SMTP log for a SMTP Virtual Server, configured from SMTP Virtual Server properties in Exchange System Manager. Exchange Server 2007 splits these into SMTP Send and SMTP Receive logs for a transport server. Gone is the per-SMTP Virtual Server granularity
(the equivalent would have been per-Receive Connector and per-Send Connector logs... note to Devin Ganger: Yes, Receive Connectors are not the same as SMTP Virtual Servers - but they're close enough conceptually to invite comparisons... :). You can still enable/disable logging for a Send or Receive Connector. For more details about SMTP Send and Receive Logs, read previous post "
Exchange Server 2007: Logging SMTP Protocol Activity".
Most settings for SMTP Send and Receive Logs are stored in the transport server configuration, just like Message Tracking Logs. However,
logging can be enabled/disabled on each individual Send and Receive Connector by using
Set-SendConnector and
Set-ReceiveConnector commands.
Location:SMTP Send Logs: \Exchange Server\TransportRoles\Logs\ProtocolLog\SmtpSend
SMTP Receive Logs: \Exchange Server\TransportRoles\Logs\ProtocolLog\SmtpReceive
Send and Receive Connector parameterProtocolLoggingLevel: None (to enable it, set it to verbose in Connector properties)
Transport Server parameters:SendProtocolLogMaxAge: 30.00:00:00
SendProtocolLogMaxDirectorySize: 250MB
SendProtocolLogMaxFileSize: 10MB
SendProtocolLogPath: \Exchange Server\TransportRoles\Logs\ProtocolLog\SmtpSend
ReceiveProtocolLogMaxAge: 30.00:00:00 (30 days)
ReceiveProtocolLogMaxDirectorySize: 250Mb
ReceiveProtocolLogMaxFileSize: 10Mb
ReceiveProtocolLogPath: \Exchange Server\TransportRoles\Logs\ProtocolLog\SmtpReceive
5. Agent Logs: Actions taken by anti-spam agents are logged in Agent Logs, and are a very welcome new addition to Exchange's messaging hygiene/anti-spam features. Agent logs are enabled by default. More about Agent Logs in previous post "
Exchange Server 2007: Managing And Filtering Anti-Spam Agent Logs".
The following agent log
parameters are not configurable.
Location: \Exchange Server\TransportRoles\Logs\AgentLog
File Size: 10 Mb
Directory Size: 250 Mb
Max Age: 30 days
Access: Agent logs can be accessed using the
Get-AgentLog shell command. There are no GUI interfaces to parse/search agent logs in the EMC.
6. Connectivity Logs: Records information about outbound SMTP connectivity to mailbox servers, smarthosts, or destination domains, including source queue, destination (mailbox server, smarthost, or domain), DNS resolution, connection failures, transmitted messages and bytes. Note, this is not SMTP (protocol) logging, but a more network-centric view of outbound connections. Connectivity Logs are not enabled by default. More details in "
Managing Connectivity Logging".
Parameters and defaults:
ConnectivityLogEnabled: false
ConnectivityLogMaxAge: 30.00:00:00
ConnectivityLogMaxDirectorySize: 250Mb
ConnectivityLogMaxFileSize: 10Mb
ConnectivityLogPath: \Exchange Server\TransportRoles\Logs\Connectivity
7. Routing Table Logs: A snapshot of the transport server's routing table is logged when the transport service starts, when a routing configuration change is detected, and at fixed interval
(12 hours by default, configurable by modifying EdgeTransport.exe.config file). More details in "
Managing Routing Table Logging".
Parameters and defaults:
RoutingTableLogMaxAge: 7.00:00:00 (7 days)
RoutingTableLogMaxDirectorySize: 50Mb
RoutingTableLogPath: \Exchange Server\TransportRoles\Logs\Routing
8. Messaging Records Management (MRM) Logs: Exchange Server 2003/2000's Mailbox Manager feature, which is often compared to Managed Folders in Exchange Server 2007, sends a report to a designated mailbox about actions taken. It also has a Report Only mode. The Managed Folders Agent, which is responsible for applying Managed Folder Mailbox Policies to mailboxes, does no such reporting. However, it does provide detailed MRM logs, which can be used to generate the required reports.
Messaging Records Management is more than simply cleaning up mailboxes. From a compliance standpoint, MRM logs are more important than others in the list. As such, it may be required to archive these for a longer period, depending on organizational policies. The MRM log defaults reflect this.
More details in "
How to Configure Messaging Records Management Logging".
Parameters and defaults:
LogPathForManagedFolders: \Exchange Server\Logging\Managed Folder Assistant
LogFileAgeLimitForManagedFolders: 00:00:00
LogDirectorySizeLimitForManagedFolders: unlimited
(per-Database, log files for the a Database have the same prefix. The limit is for log files for each Database, not a cumulative size limit for the directory)LogFileSizeLimitForManagedFolders: 10MB
MRM logs are disabled by default. To enable MRM logging, set any of the following parameters to true.
RetentionLogForManagedFoldersEnabled: False (Set to $true to enable logging of messages processed because they reached the retention limits)
JournalingLogForManagedFoldersEnabled: False (Set to $true to enable logging of items in Managed Folders are journaled)
FolderLogForManagedFoldersEnabled: False (Set to $true to log creation or deletion of Managed Folders by
MFA)
SubjectLogForManagedFoldersEnabled: False (Set to $true to log subject of messages being processed by MFA)
9. IIS Logs: On Client Access Servers, HTTP activity for
OWA and
EAS access is logged in IIS logs. Configuration of IIS logging is controlled from the IIS Manager console. IIS activity can be logged in a number of different log file formats:
- the default
W3C Extended (ASCII text, fields customizable)-
IIS (fixed field, ASCII text, not customizable)-
NCSA Common (fixed field, ASCII text, not customizable)- and
ODBC (logged to ODBC-compliant databases like Microsoft Access and SQL Server, resource-intensive).
Path: %systemroot%\System32\LogFiles\W3SVC1 (where 1 is the web site ID in IIS Metabase)
Max File Size: Unlimited. Log files rolled over daily. Setting can be changed to roll over log files based on file size.
Max Directory Size: unlimited (Cannot be set. It's important to remove/archive these periodically.)
More info about configuring IIS logs in "
Configuring IIS Logs (IIS 6.0)".
IIS Logs and Exchange ActiveSync: Exchange Server 2007 also has a cmdlet/task for extracting ActiveSync data from IIS logs and generating reports -
Export-ActiveSyncLog. More info about EAS reporting in
Exchange ActiveSync Reporting Services.
10. POP3 and IMAP4 Protocol Logs: Protocol logging for POP3 and IMAP4 protocols is
disabled by default. This can be enabled by
editing the related config files. The logs are not kept around for too long - the default is 24 hours, just enough to allow for troubleshooting recent issues. In most environments, these logs lose value quite rapidly - keeping them for extended periods is unnecessary, unless mandated by compliance policies in your organization.
POP3 log configuration: Microsoft.Exchange.Pop3.exe.config file
IMAP4 protocol log: Microsoft.Exchange.Imap4.exe.config file
Location: \Exchange Server\ClientAccess\PopImap
Parameters and defaults:
ProtocolLog: false (disabled by default, change this key to true in above config files for each protocol to enable logging)
AgeQuotaInHours: 24 hours
SizeQuota: 10000000 (10 million bytes / approx 9.54 Mb)
PerFileSizeQuota: 1000000 (1 million bytes / approx 976 Kb)
11. Certificate Logging: Certificate logs can be used to troubleshoot certificate-related problems for SMTP, POP3 and IMAP4 protocols. Though certificate-related issues are logged in the Application Event Log,
Exchange Server 2007 SP1 adds the functionality to log more detailed information to a log file. In addition to the above, verbose information can be exposed/output in the Exchange shell when using the Get-ExchangeCertificate, New-ExchangeCertificate, and Enable-ExchangeCertificate commands, by adding an xml snippet to the Powershell.config file. The configuration options are discussed in "
How to Enable Certificate Logging" in Exchange documentation.
12. Cluster Log: In clustered environments, Windows Server 2003/2008
OS maintains a cluster log with detailed information about cluster events like initialization, node addition/removal, resource states, failovers, etc. The Cluster service also logs important event information to Windows event logs. However, for in-depth troubleshooting and diagnostics, the cluster log has the beef. More information about the Cluster log in "
Cluster Log Basics".
Location: %systemroot%\Cluster
13. Pipeline Tracing Logs: Pipeline tracing is
used to troubleshoot transport agents. It logs email messages as they traverse the transport pipeline, including message content and actions taken by transport agents. Pipeline tracing is configured using the Set-TransportServer command.
More info in "
Using Pipeline Tracing to Diagnose Transport Agent Problems".
Parameters:
-PipelineTracingEnabled: false (set to $true to enable Pipeline Tracing)
- PipelineTracingPath: location of Pipeline Tracing logs, default \Exchange Server\Transport Roles\Logs\PipelineTracing
- PipelineTracingSenderAddress: Use internal or external sender's SMTP address to log messages sent by that address. Only messages sent by that address are logged, including message content. Use "<>" to log system messages like OOFs, DSNs, journal reports, etc. (Logs *all* server-generated messages a Hub Transport server sees - can place significant load on the server).
14. Application Event Log: Last, but not the least, Exchange logs plenty of information to the Application Event Log. The level of logging is set to lowest for most Exchange services and processes. Each event log entry has a numeric identifier - the Event ID, and a well-defined structure. Events in Windows event logs can be accessed using the Event Viewer console, which provides a rich
UI for viewing, searching and filtering event log entries. Other acess methods include interfaces like WMI. Windows PowerShell (and therefore, the Exchange shell) also provide a way to quickly access event log information from the command-line, using the
Get-EventLog command.
Diagnostic Logging and Exchange Server 2007: Every once in a while you run into issues that require more information from different Exchange services/processes, than what's logged to the Application event log by default, in order to troubleshoot them. Such detailed logging is not required for normal operations.
Diagnostic Logging levels: You can change the level of detail Exchange services/processes log to the Application Event Log when diagnostic logging is enabled. The different levels:
0 - Lowest
1 - Low
3 - Medium
5 - High
7 - Expert
If left turned on, diagnostic logging can quickly flood event logs, making it difficult to locate other important events or having them purged from logs based on size and age restrictions. Bump up diagnostic logging to troubleshoot issues, and remember to turn it off once done.
To bump up diagnostic logging for a particular Exchange process/service (
here's a list of processes with configurable event log levels) - the Categorizer in this case, to level 7 (expert):
Set-EventLogLevel MSExchangeTransport\Categorizer -Level 7
More information about diagnostic logging in "
Diagnostic Logging for Exchange Processes".
In addition to the Application event log, the OS also maintains Security and System event logs.
 Are you log happy?:
Are you log happy?: By all accounts, Exchange Server 2007 is a
log-happy product, providing a rich set of logs for its different features, services and processes. In many cases , parsing these logs is made much easier than previous versions, thanks to the Exchange shell commands and changes to logged fields/formats.
Whereas logs like Windows Servers' event logs provide a rich user interface
(further enhanced in the new Event Viewer in Windows Server 2008) and access methods, and others like anti-spam Agent Logs can be accessed and parsed easily using the Exchange shell, there are plenty of logs in the above list that are not accompanied by any specific user interfaces or shell commands. In particular, the SMTP (Protocol) Send and Receive log is one such that is accessed frequently by administrators while troubleshooting mailflow issues. Hopefully, future versions of Exchange will include the necessary shell commands to access and parse these.
Nevertheless, it is great to have access to more information for troubleshooting and operations, provided you know where to look.
Labels: Administration, Exchange Server 2007

 Exchangepedia Blog is read by visitors from all 50 US States and 150 countries world-wide
Exchangepedia Blog is read by visitors from all 50 US States and 150 countries world-wide


 Create a new
Create a new 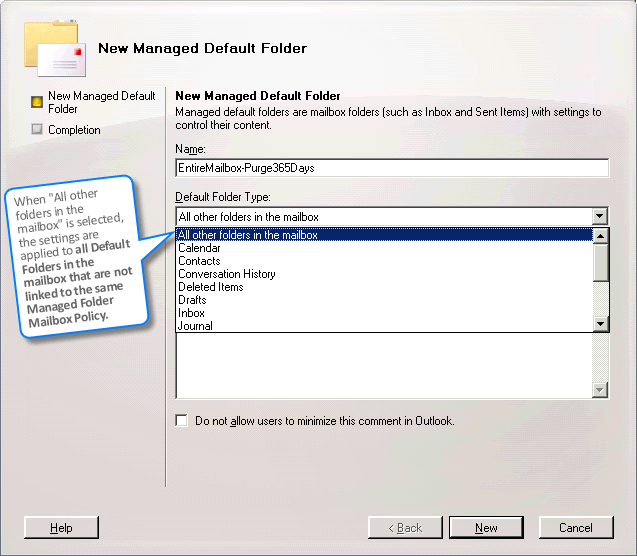
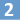 Create new Managed Content Settings for the new folder. Under message type, select "E-mail".
Create new Managed Content Settings for the new folder. Under message type, select "E-mail".
 Add this new Managed Default Folder to an existing
Add this new Managed Default Folder to an existing  Apply the policy to appropriate users if not already applied.
Apply the policy to appropriate users if not already applied.  Ensure the Managed Folder Assistant is scheduled to run.
Ensure the Managed Folder Assistant is scheduled to run. 
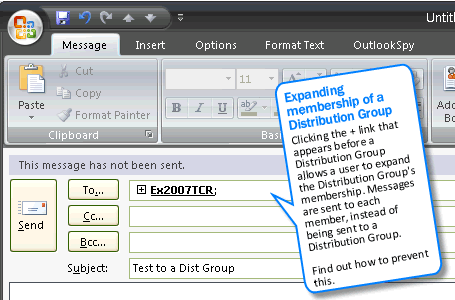
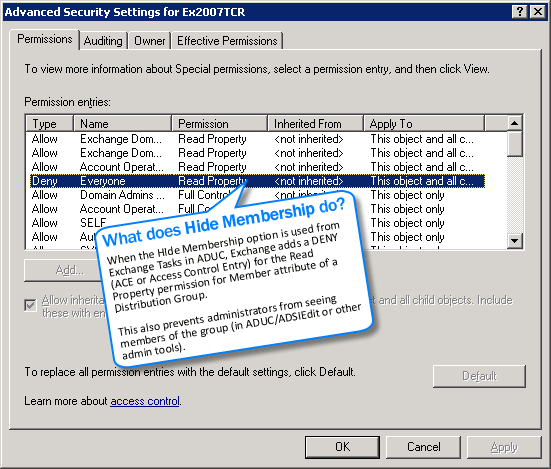
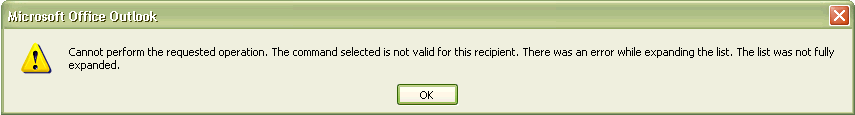
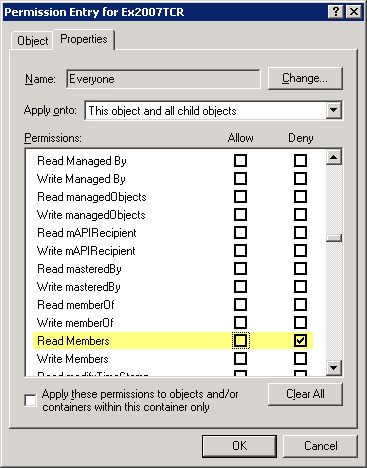 1. Navigate to the Distribution Group's properties
1. Navigate to the Distribution Group's properties