Social engineering is all about psychological attacks— convincing a user to willingly divulge information is much more convenient, in most cases, than actually brute-forcing your way in. Attackers with very little technical sophistication (and perhaps some great social skills) can easily prey upon even the more vigilant users. I would’ve held on to my belief in the user’s intellect — most users are smart enough to recognize these social engineering attempts, but developments in recent years involving quite a few internet-savvy users around me have forced me to change my opinion.
A mailbox quota message from an unknown source just popped up in my mailbox. Probably the first time I’ve seen a social enginering attack disguised as a mailbox quota message. OOFs are probably next on the list.
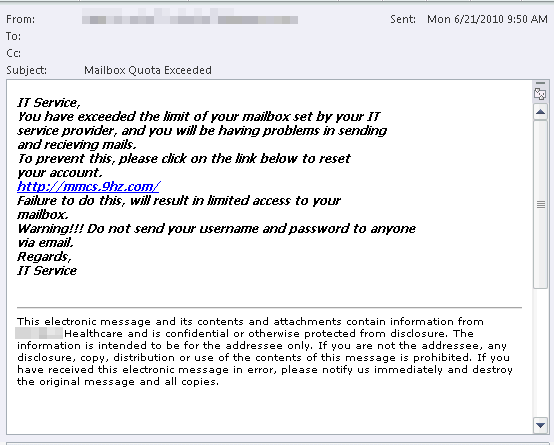
Figure 1: A fake mailbox quota message with a suspicious URL
The fake quota message includes a suspicous-looking link leading to an external web site. Of course, most IT organizations encourage users not to click on links in such messages. If the message is flagged as spam, the links would not be active when viewed in Microsoft Outlook or Outlook Web App (OWA – formerly Outlook Web Access), so this applies only to messages that do make it through your anti-spam filters. In this case, the link leads to a web site with a form that asks for the user’s email address, username and password.
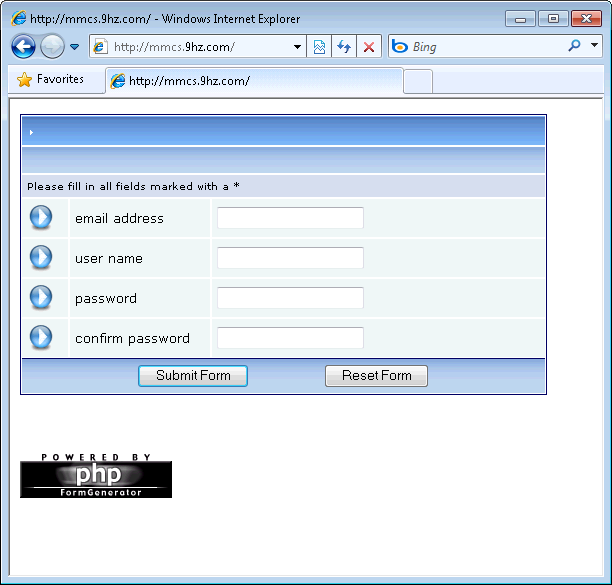
Figure 2: The URL in the fake quota message leads to a web site that asks for credentials
What can you do to protect your users
You can take a number of steps to protect your users from such attacks. The first step would of course be to stop such messages from getting to your users’ mailboxes. Your antispam/antimalware filter is the first defense against such attacks. Next, you can use a transport rule to block messages from outside the organization containing particular verbiage such as “Mailbox Quota Exceeded”. (Given the variations in verbiage that such messages could have, this may not be a very practical or long-term solution. As with any static lists, you would need to keep the list of keywords/phrases updated. Regular expressions may offer some relief.)
However, the best protection against social engineering attacks is to educate users. A genuine mailbox quota message has some distinguishing characteristics.
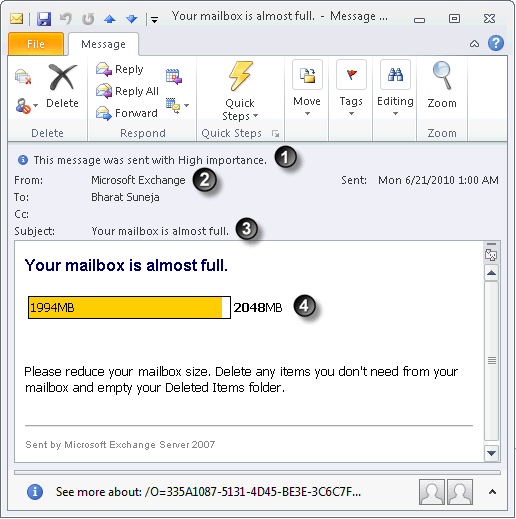
Figure 3: A genuine mailbox quota message has distinguishing characteristics
- Mailbox quota messages are sent with high importance
- Mailbox quota messages are sent only by Microsoft Exchange
- Quota message subject can’t be customized and is limited to what’s hard-coded in Exchange. Users will only see the quota message corresponding to the quota event, as listed in the table below. See Understanding Quota Messages for details.
Event Message subject Mailbox of unlimited size exceeds its Issue Warning quota Your mailbox is becoming too large Mailbox of limited size exceeds its Issue Warning quota Your mailbox is almost full Mailbox of limited size exceeds its Prohibit Send quota Your mailbox is full Mailbox of limited size exceeds its Prohibit Send and Receive quota Your mailbox is full - Quota messages include a graphical representation of mailbox quota and available space (unless the mailbox size is unlimited)
- You can customize quota messages to add additional text, including appropriate internal URLs with more helpful description, actions to take, and helpdesk contact information. This text can also help users recognize authentic quota messages from your organization. For more details about customizing quota messages, see Understanding Quota Messages, and New-SystemMessage cmdlet reference.

{ 0 comments… add one now }