Adrienne Porter Felt, an engineer on Google’s Chrome security team, recently found in-flight WiFi service provider GoGo using a fake certificate for Google.com and tweeted the following, with a screenshot.
hey @Gogo, why are you issuing *.google.com certificates on your planes? pic.twitter.com/UmpIQ2pDaU
— Adrienne Porter Felt (@__apf__) January 2, 2015
If you’re a GoGo customer, here’s why you should be concerned.
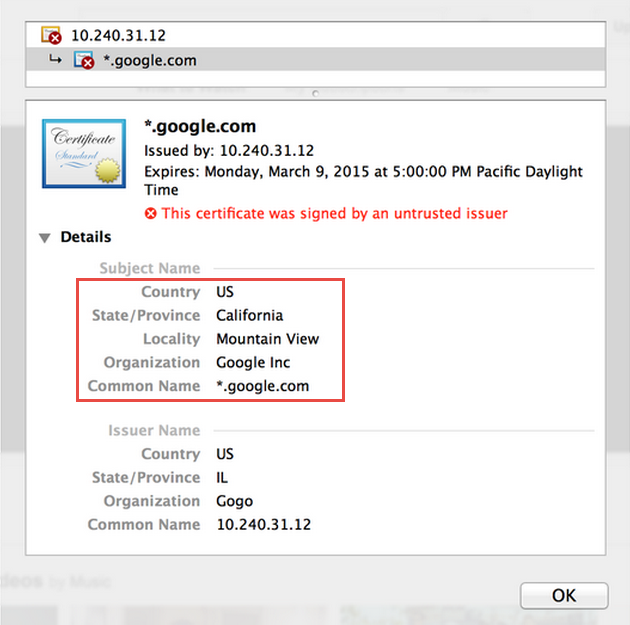
GoGo used a fake wildcard certificate – a certificate issued for all Google domains (*.google.com). This gives them the ability to intercept/decrypt all SSL-encrypted traffic to Google services.
Is it really a Man-In-The-Middle attack?
Some in the IT and security communities argue that it’s not a man-in-the-middle attack. Some of the reasons provided:
1. It’s GoGo’s network and they’re authorized to do whatever they want on their own network.
2. It’s a common practice – many corporate networks intercept and decrypt their users’ encrypted traffic.
3. It’s a valid method for detecting and blocking streaming video and thereby preventing misuse of their network. This is also the reasoning GoGo uses in its response.
4. Web browsers do warn you about the certificate (as Chrome did in this case).
5. If you don’t like it, don’t use it.
What’s a man-in-the-middle attack? Quite simply, it’s when a third entity inserts itself between you and the person or service you’re communicating with, and is able to intercept, monitor, capture or control the communication by impersonating as one of the parties.
Google described an attempted man-in-the-middle attack a few years ago when fraudulent certificates for Google.com issued by certification authority DigiNotar were used. GoGo uses self-signed certificates.
Web browsers warn against certificates not issued by a trusted certification authority, but the warning is generally ignored by most users.
The questions we should ask:
- Is GoGo using a fake SSL certificate and impersonating a third party (Google)?
- Is GoGo decrypting encrypted communication between its customers and Google?
- Is Gogo monitoring, inspecting or capturing the decrypted communication?
Sure, it’s GoGo’s own network, but unlike businesses that provide network access to their employees, who are subject to their accepted corporate policies, GoGo is a paid service provider. Intercepting encrypted traffic is not something one expects from a service provider.
You could give GoGo benefit of the doubt and assume there was no malicious intent and that GoGo isn’t inspecting or capturing your personal data including passwords. But decryption of encrypted traffic between two entities by a third party without their explicit consent or knowledge is unethical and should be illegal.
Regardless of whether GoGo saves the decrypted communication or not, or whether it uses the decrypted data for a malicious purpose or not, GoGo’s behavior meets the definition of a MITM attack.
When asked if it’s indeed a Man-In-The-Middle attack, noted security guru Bruce Schneier agrees:
Of course it is (a man-in-the-middle attack). It is the very definition of how a man-in-the-middle attack works. If I were to explain it to students, I could easily use this as an example.
– Bruce Schneier
Roger A. Grimes, security columnist for InfoWorld magazine, doesn’t feel as strongly:
It’s a bit strong to call it a MitM attack, although I guess you could. But MitM attacks are also about intent, and their intent wasn’t purely malicious.
– Roger A. Grimes
GoGo’s response
GoGo responded with a statement about its streaming video policy from Executive Vice President and CTO Anand Chari. Chari defends it as a valid method to prevent users from accessing streaming video services:
…we don’t support various streaming video sites and utilize several techniques to limit/block video streaming. One of the recent off-the-shelf solutions that we use proxies secure video traffic to block it.
Interestingly, Chari makes no mention of the fake certificates.
But GoGo’s Terms of Use indicate they do allow streaming, as long as the videos are of a duration less than five minutes! Besides, there are other, more efficient ways of preventing streaming or slowing down bandwidth hogs on flights. Gogo’s Terms of Use also indicate it uses techniques such as throttling to control bandwidth usage and that customers should expect reduced speeds after five minutes of streaming video in an hour or 8 MB of file downloads.
The right thing to do is to not use fake certificates to inspect its customers’ traffic. But if GoGo insists on taking that route, the least it can do is clearly indicate that it will be inspecting customer traffic to some/all destinations to ensure some users are not hogging bandwidth. This includes decryption of SSL-encrypted traffic between a GoGo user and the site or service they’re communicating with. The info should be clearly displayed when a new user signs up for GoGo service and every time users log-in to the service.
If GoGo insists on taking that route, the least it can do is clearly indicate that it will be inspecting customer traffic.
Grimes agrees: “In general, it’s never a good idea for companies that don’t own domains to be creating certificates bound to those domains. It’s certainly not a best practice and the impacted domain owners certainly are never going to agree. Most of this would be a non-issue if it was explicitly communicated to all involved parties, and not just in tiny writing or a EULA. This isn’t the right way for Gogo to go about what they were trying to accomplish, but I’m not that upset over it either, because of the purposed motivation.”
Until GoGo fixes it or gives a clear indication, I’ll give in to the last argument and not use their service. If you do use it, a more secure option may be to connect to your company’s VPN or one of the free VPN services.

{ 1 comment… read it below or add one }
If it looks like a skunk, smells like a skunk….