Exchange 2010 includes Administrator Audit Logging functionality to log all administrator actions. Because all administrator actions, including those taken using the EMC and the new web-based ECP consoles must fire off a Shell command under the hood, admin audit logging records cmdlets that can make changes (the ones that use the New and Set verbs, for example — New-Mailbox, New-DistributionGroup, Set-ReceiveConnector, etc.).
However, changes to Exchange configuration and recipient objects, which reside in Active Directory, can also be made directly in Active Directory if an administrator has adequate permissions. Whereas it’s not a good idea to make such changes to most Exchange Server configuration settings and recipients directly by modifying Active Directory objects, tasks such as modifying group memberships are possible using tools like Active Directory Users & Computers, ADSIEdit, or programmatically using the Active Directory Services Interfaces (ADSI) provider. Such modifications bypass Exchange 2010’s Role-Based Access Control mechanism, and thereby the admin audit logging functionality.
To audit changes to Active Directory objects, you must enable auditing in Active Directory. Let’s take a look at how this can be done in Windows Server 2008 and later.
Task 1: Enable Auditing of Active Directory service access in the Default Domain Controller Policy
- Fire up the Group Policy Management Console (GPMC)
- Expand the domain you want to manage and select the Domain Controllers OU
- In the Linked Group Policy Objects tab, right-click the Default Domain Controllers policy | select Edit
- In the Group Policy Management Editor, expand Computer Configuration | Policies | Security Settings | Local Policies | Audit Policy
- In the details pane, double-click Audit directory service access
- In the Properties page, select Define these policy settings, and in the Audit these attempts: section select Success
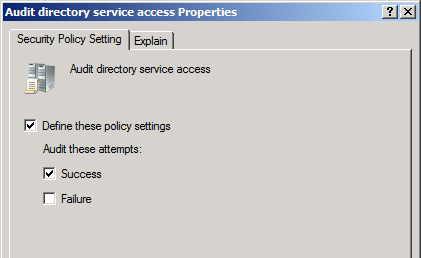
Figure 1: Enable auditing of directory service access in the Default Domain Controllers policy
Task 2: Enable auditing of directory service changes
In Windows Server 2008 and later, you can enable auditing of Directory Service Changes, a sub-category of directory service access. This records object creation, modification, moves and undeletes. The event log entries include information about the old and new values of the parameter modified. In case of multi-valued attributes such as the member attribute, one event log entry is recorded for each value (each group member) that’s added or removed, even if you add/remove multiple values in a single operation. You can enable auditing of Directory Service Changes using the auditpol.exe command.
Auditpol /Set /Subcategory:”Directory Service Changes” /Success:Enable
Common Audit Policy tasks
- List current audit policy for all categories/sub-categories: AuditPol /Get /Category:*
- List all sub-categories you can enable auditing for: AuditPol /List /SubCategory:*
- Enable auditing of a subcategory for successful and failed attempts: AuditPol /Set /SubCategory:”subcategory name” /Success:Enable /Failure:Enable
- Backup audit policy settings to a text file: AuditPol /Backup /File:MyAuditPolicy.txt
- Clear audit policy settings: AuditPol /Clear
Task 3: Configure auditing of distribution group membership changes
After you enable auditing policy in your Active Directory domain, you must configure the objects you want to audit — in this case, group objects. You can do this at a number of levels:
- At the object level, in the properties of the particular distribution or security groups you want to audit
- At the parent container level, in the properties of an OU or container
- For the entire domain
In this example, all our distribution groups are located in the Distribution Groups OU. We’ll configure the OU to apply auditing settings to all its descendant (child) group objects. Further, the specific event we want to audit is use of Write Member permission to modify the Member attribute of groups.
You can also enable auditing of additional or all events, but auditing events that have little security or compliance value to your organization generates significant auditing noise, which makes locating the important events harder. Additionally, it’s resource-intensive — the higher volume of logs it may generate will need to be stored or archived for some time, depending your organization’s requirements. Needless to say, searching larger data sets is slower.
Make sure auditing requirements are clearly outlined and understood before enabling auditing.
- Start Active Directory Users & Computers console and navigate to the OU or container for which you want to configure auditing (Distribution Groups OU in this case).
- Right-click the OU | select Properties | select the Security tab | click Advanced
- On the Auditing tab, click Add
- In the Enter the object name to select box, type Everyone | click OK
- In the Auditing Entry for Distribution Groups window, select the Properties tab
- From the Apply onto: drop-down control, select Descendant Group objects
- In the Access section, scroll down to locate the Write members entry, and select Successful
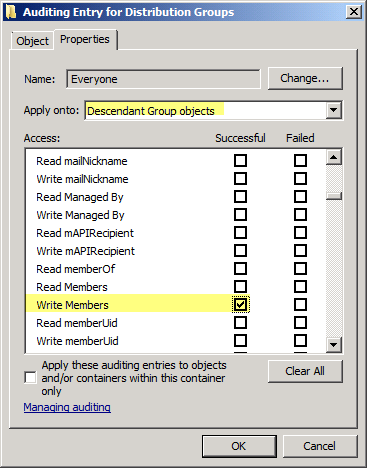
Figure 2: You can configure auditing granularly at the object (security/distribuiton groups) level, at the OU or container level, or for the entire domain. In this example, auditing of successful use of Write Members permission is enabled.
Monitoring distribution group membership changes
After you enable auditing of group membership changes, any changes to the member attribute are logged in the Security event log. Event ID 4662 is a notification event which notes that changes have been made, but isn’t very useful otherwise. Event ID 5136 (see screenshot below) shows you name of object, object attribute modified (member), Operation performed (value added), and the value which was added (distinguishedName of user added to the member attribute).
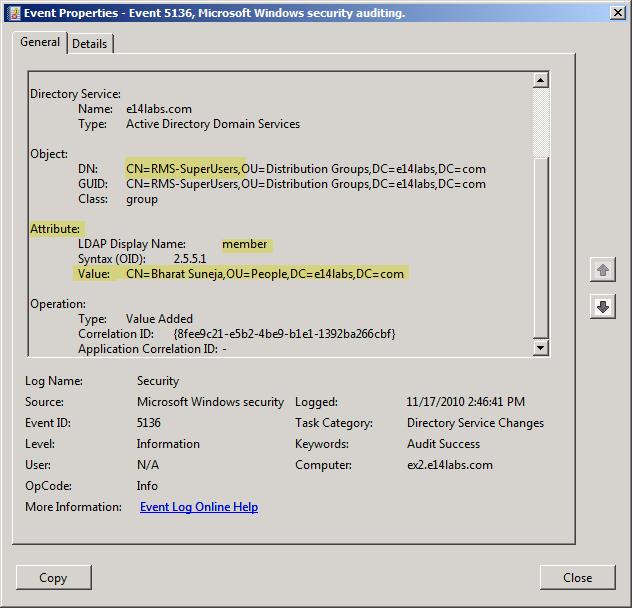
Figure 3: Event ID 5136 logged in the Security event log provides detailed audit information about group membership changes, such as object modified, attribute modified, type of operation, and value added/removed.
Searching event logs using the Shell
Shell jockeys can use the Shell to search the event logs. In PowerShell v2, the Get-EventLog cmdlet provides more filtering capability for searching event logs, including the much needed capability to search by the Event ID (thanks PS folks!).
This command searches the Security event log for Event ID 5136 that occurred after Nov. 15th. The InstanceID parameter is used to specify the Event ID.
Get-EventLog -LogName Security -EntryType SuccessAudit -InstanceID 5136 -After “11/15/2010”

{ 5 comments… read them below or add one }
Excellent post!
great post, thanks!
ADAudit Plus is a valuable security tool that will help you be compliant with all the IT regulatory acts. With this tool, you can monitor user activity such as logon, file access, etc. A configurable alert system warns you of potential threats.
I personally use Lepide AD auditor to monitor the changes made in active directory. It has centralized system auditing feature that helps to audit all domains in the network at a centralized location and sends real-time alerts of all critical changes instantly by customized email notification. Thus, we can see a clear picture of the AD object status for every second.
Nice post, thanks for sharing this article, I tried this LepideAuditor Suite( http://www.lepide.com/lepideauditor/) for this. This software helps me to audit Group Policies and get the complete detail who is doing what, when, and from where.