On Thursday, WordPress.org released WordPress 4.7.2, fixing the following four vulnerabilities.
- The user interface for assigning taxonomy terms in Press This is shown to users who do not have permissions to use it. Reported by David Herrera of Alley Interactive.
- WP_Query is vulnerable to a SQL injection (SQLi) when passing unsafe data. WordPress core is not directly vulnerable to this issue, but we’ve added hardening to prevent plugins and themes from accidentally causing a vulnerability. Reported by Mo Jangda (batmoo).
- A cross-site scripting (XSS) vulnerability was discovered in the posts list table. Reported by Ian Dunn of the WordPress Security Team.
- An unauthenticated privilege escalation vulnerability was discovered in a REST API endpoint. Reported by Marc-Alexandre Montpas of Sucuri Security.
The REST API vulnerability, which affects two previous WordPress builds that have the API enabled by default (WP 4.7 and 4.7.1), was reported by Sucuri. It allows an unauthenticated user to modify the content of any post or page within a WordPress site.
As noted in the original release, public disclosure of the REST API vulnerability was delayed. WordPress shares the details of the disclosure process in Disclosure of Additional Security Fix in WordPress 4.7.2. Responsible disclosure of a vulnerability allows stakeholders reasonable time to mitigate risks (create, distribute and apply patches or take other steps to harden) before public disclosure occurs.
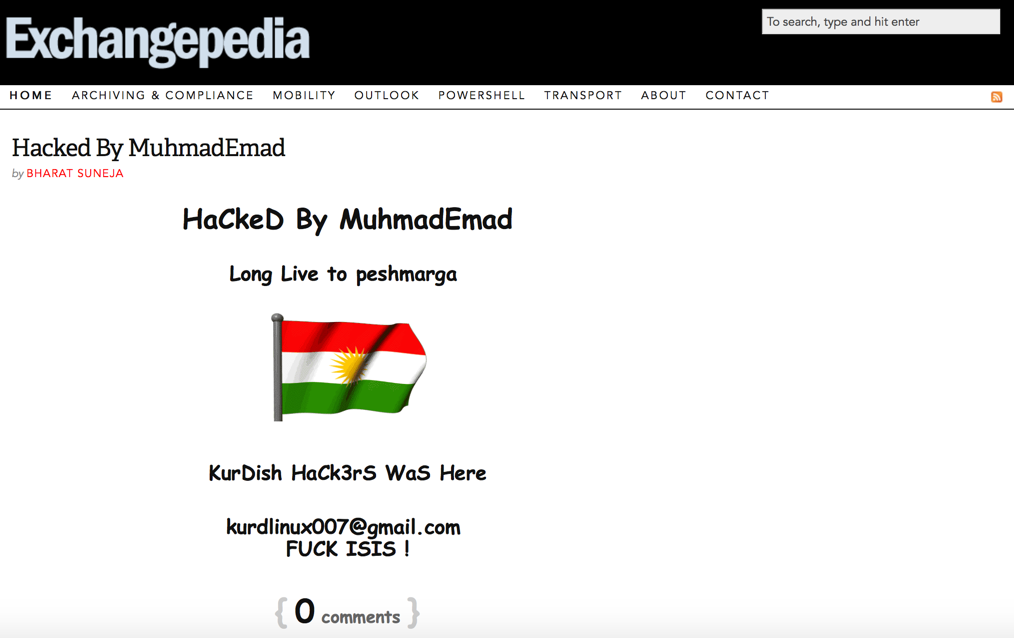
WordPress instances that are configured to update automatically got the update shortly after WP 4.7.2 was released on Thursday (2/2). The WordPress instance running this site had automatic updates disabled, and became an easy target. The attacker altered content of the latest post, as shown int the screenshot.
The issue has been fixed and the altered post content restored. If you see content similar to the above screenshot on any page, please leave us feedback in post comments on the affected page or here.
Disabling REST API in WordPress
Interestingly, there’s no setting to disable the REST API in WordPress. This has been a topic of discussion among WordPress developers and community.
Before WordPress 4.7, you could disable the REST API by adding the following lines to the WordPress instance’s functions.php file. It uses the rest_enabled filter. More details in Robert Abela’s article here.
add_filter(‘rest_enabled’, ‘_return_false’);
add_filter(‘rest_jsonp_enabled’, ‘_return_false’);
WordPress is likely to see more REST integrations and dependencies, so disabling REST API is not recommended. The rest_enabled filter has been deprecated in WordPress 4.7.
As always, it’s critical to keep software updated. That’s as true for WordPress as it is for operating systems, platform components, middle ware and applications. WordPress’ automatic update functionality seems to have worked for most users, but there’s likely a significant number of WordPress sites that don’t have it enabled.

{ 0 comments… add one now }